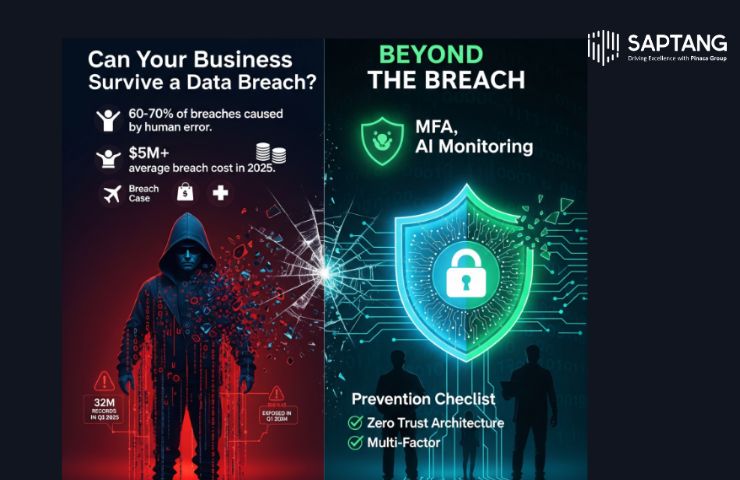
Beyond the Breach: Increasing Security Measures to Prevent Data Leaks in the Digital Environment
Beyond the Breach: Increasing Security Measures to Prevent Data Leaks in the Digital Environment By- Karthikeyan Sachithanandam Data is more than just information in the hyperconnected digital world of today; it’s also identity, continuity, and trust. Customer confidence is reflected in every piece of personal information entrusted to a business. However, the digital world feels