By Karthikeyan Sachithanandam, Researcher
Data is more than just information in the hyperconnected digital world of today; it’s also identity, continuity, and trust. Customer confidence is reflected in every piece of personal information entrusted to a business. However, the digital world feels more vulnerable in a time when even a small mistake can result in disastrous exposure.
Data is being stolen, sold, and exposed at startling rates, ranging from millions of people’s medical histories to their personal shopping preferences. A real person someone whose privacy was violated, whose financial life was upended, and whose trust may never be restored lies behind every breach of statistics.

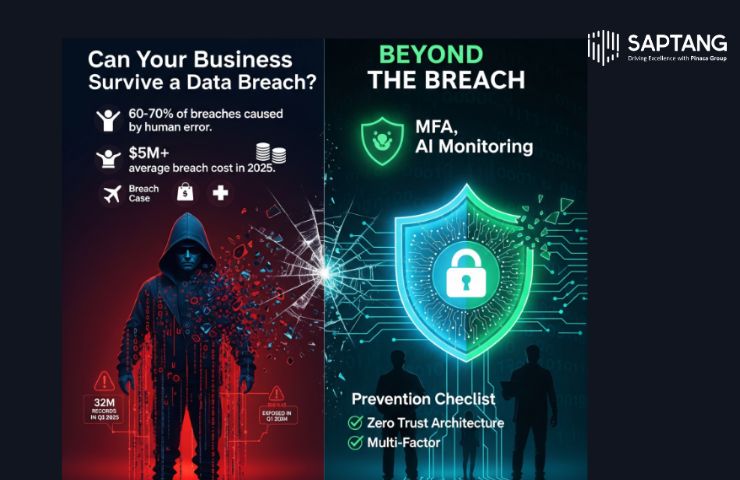
The number and scope of data compromise incidents have alarmingly increased, according to our analysis of breach trends in early 2025. Over 32 million people’s personal information was impacted by 658 breaches that were formally documented in the first quarter alone. Parents, students, patients, and travelers are among the 32 million people who were impacted in very personal ways but had no say in the loss of their data.
Millions of private documents were unintentionally made public in a number of these incidents, exposing long-standing flaws in digital systems. Despite its innovation, the modern organization’s digital transformation frequently surpasses its capacity to protect what is most important.
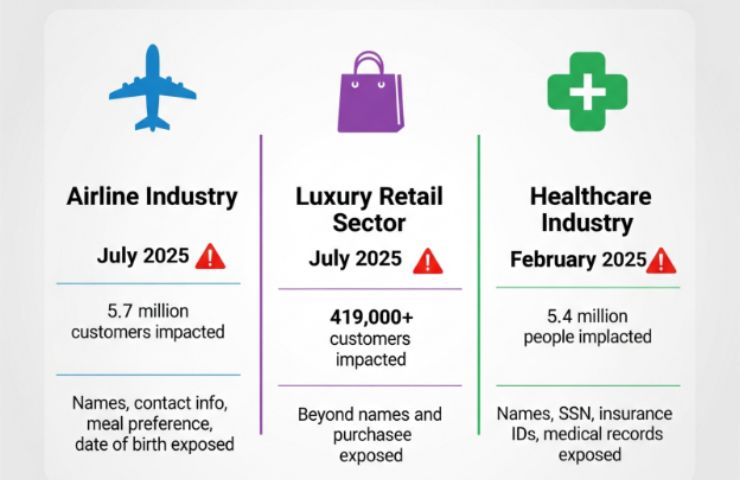
Airline Industry (July 2025)
An estimated 5.7 million customers were impacted because of a breach that was confirmed by a major international airline. Among the information made public were names, contact information, meals preference and date of birth. Imagine a family planning a long-awaited trip only to find out that a system they trusted had compromised their personal information.
More than 419,000 customers in one region were impacted by a breach disclosed by a well-known international fashion conglomerate, with indications of a wider global impact. The hack revealed how even luxury can become vulnerable in the wrong hands, going beyond names and purchases. Public anger and anxiety were only heightened by delays in disclosure violations.
A breach at a major healthcare analytics provider exposed the data of 5.4 million people, including Names, Social Security Numbers, Insurance IDs and medical records. This was about patients, not just stolen data. People who seek medical attention and entrust healthcare systems with their most private information only to have that trust betrayed.

Data breaches are emotional injuries in addition to technical ones. People feel vulnerable, scared, and helpless when their personal information is stolen. The impact on a company’s finances and reputation is disastrous. According to our research, the average cost of a data breach worldwide in 2024 was about $4.88 million, and projections indicate that by the end of 2025, this amount may surpass $5 million.
However, there are actual repercussions that go beyond statistics and audits, including regulatory inquiries, court cases, declining stock values, and most painfully a decline in customer confidence. Years of brand loyalty and moral reputation in the eyes of customers can be destroyed by a single violation.
It’s critical to understand that elite hackers are not responsible for every breach. The main offenders continue to be human error, weak passwords, reused credentials, inadequate vendor oversight, and slow response times. Our research shows that human factors account for between 60 and 70 percent of breaches, and third-party vendors are responsible for almost 30 percent of them. These findings clearly highlight the need for improved oversight, training, and communication.
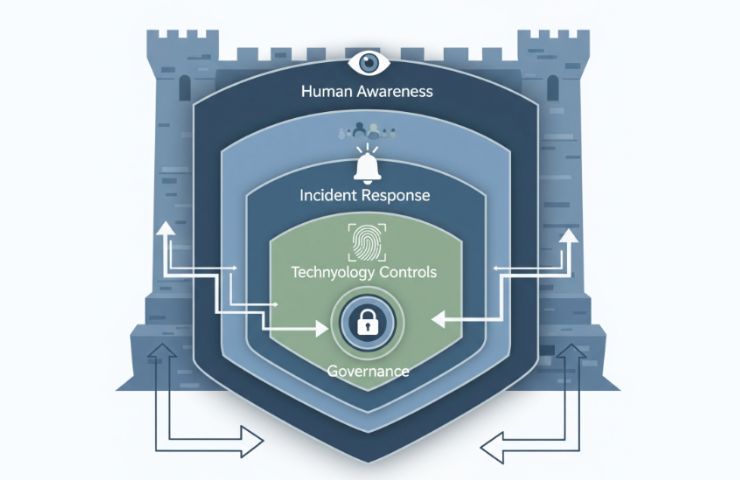
A successful data defense strategy needs to be multi-layered, proactive, and comprehensive, as our in-depth research and real-time threat monitoring confirm. Security is a cultural issue as much as a technical one.
The foundation of any organization’s data security strategy must be policy and accountability. To increase resilience, reduce blind spots and find gaps by conducting routine audits and risk assessments.
The armor is technology, but it needs to be updated and refined continuously:
In the digital battlefield, these are shields as well as tools.
Minutes are crucial when there is a breach. The difference between containment and disaster can be determined by a prompt, coordinated response:
Every second matters, and whether you come out stronger or broken depends on how prepared you are.
The culture of the company needs to be infused with security awareness. No firewall can prevent a thoughtless click, but training can:
Keep in mind that your people are either your best line of defense or your biggest vulnerability. Give them the appropriate amount of power.
While the digital age offers tremendous potential, it also exposes businesses to never-before-seen risks. A data breach has an operational and emotional cost that goes well beyond news reports and boardroom debates.
Data leaks affect more than just systems; they affect people’s lives, from hospital patients to upscale boutique customers and travelers. Even though no organization is impervious, those that put a high value on resilience, trust, and openness will fare much better than those that don’t.
Our study emphasizes a straightforward reality: cybersecurity is a human commitment as much as a technical endeavor. Data protection entails protecting privacy, dignity, and the common vision of a safer digital future.
Businesses that adopt this perspective and make security ingrained in their culture will increase trust while reducing breaches. And ultimately, the most precious resource of all is trust.
You may also like to read about this: The Digital Exploitation of IRCTC and the Silent Collapse of Trust in Public Infrastructure