
By Giridharan S, Cyber Researcher
Overview Advanced Persistent Threat (APT) groups are among the most capable and persistent opponents in the unpredictable and dangerous realm of cyberwarfare. APT campaigns can involve targets of huge consequence, e.g., governments, businesses, vital infrastructure or even sometimes individuals; there is a tendency to conflate espionage with sabotage and war. However, for the uninitiated, “APTˬ” might seem confusing, while the technologists overseas are preoccupied with the pieces of malware, intrusions, and identifying command and control and zero days. The Cyberwarfare Chess Masters: An Inside Look at APTs Headlines about hacks and stolen data or disrupted services are easily identifiable to non-technical readers these days. This article seeks to offer bite-sized content for both audiences, without pedantic technical details or overly dramatic narrative.
An APT is simply a well-funded group of coordinated hackers who conducts focused, prolonged intrusions rather than a single guy. APTs move with intention as opposed to smash-and-grab attacks where bad-actors are working to capture any weak system spread across a large area:
Advanced: APTs use both the well-known tools everyone else uses, but they also create their own malware, at times exploiting something that is undiscovered (zero-day) security vulnerability.
Persistent: They can be relentless for months or years with planning, reconnaissance, and intermittent changes to remain undetected.
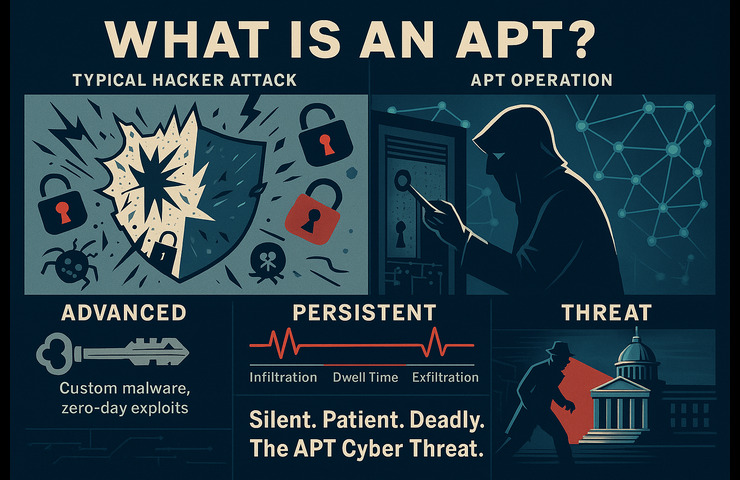
Threat: They are a significant threat to intellectual property, business continuity, and national security.
To the general public, APTs are like clandestine intelligence operations – like spies who don’t just charge in guns blazing. They create safe houses (compromised systems), and conduct careful, random infiltration, picking off bits of information slowly over time. Technologists think of laterally moving across networks, using encrypted channels and employing layers of stealth malware, all connected to a player who considers cybersecurity a game of chess.
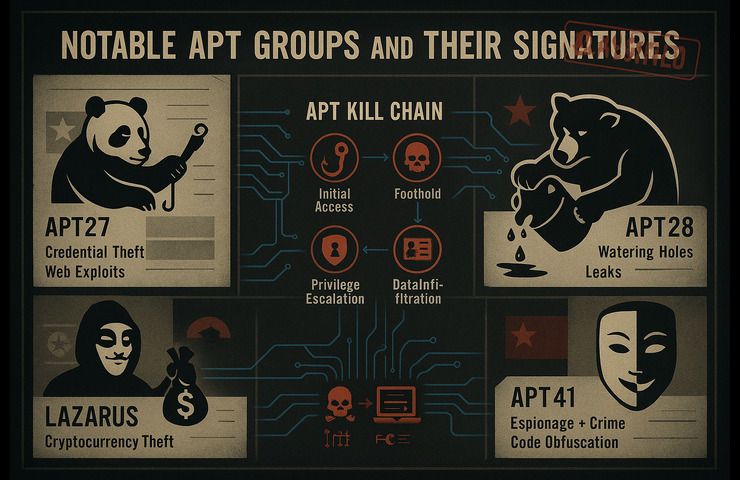
There are two notable APT organizations and their signatures Even though there have been dozens of APTs identified over the last ten years, there are some that have consistent notoriety:
Typical signature features include remote access Trojans (RATs), web-facing application exploits and sensitive documents that contain stolen information.
The Cyberwarfare Chess Masters: An Inside Look at APTs3 Spear-phishing using convincing email lures and custom backdoors that dormantly lie dormant for weeks before activating are examples of signature tactics.
Exploiting common web-server vulnerabilities, compromising public websites to conduct watering-hole attacks.
Supply-chain attacks targeting software updates; Ransomware operations
Expert use of code obfuscation, by combining public and private code exploit frameworks to mask identity, is among their signature tactics.
Each of these groups has its own “playbook,” but they all have representative play-by-play steps through which they pass, typically: gaining access, establishing a foothold, escalating privileges, finding valuable data, and exfiltrating the data over stealth channels or with encryption.
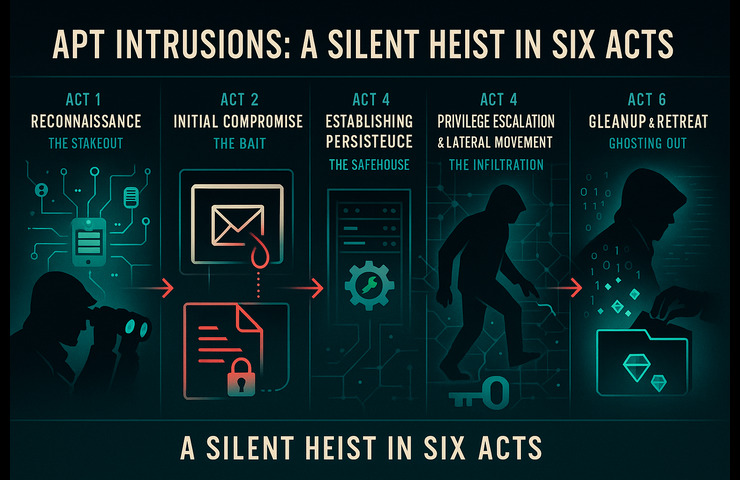
Technically, it would be counter productive to address exploit code or packet captures, so let us simply provide an overview of the lifecycle of a typical APT intrusion.
Attackers systematically enumerate their victim’s digital surface area, including employee social media postings, public-facing servers, published email addresses, and so forth.
An executive receives an authentic-looking email suggesting a trusted vendor relationship. The executive clicks the attachment, and a hidden connector to the attacker’s servers goes live.
Even if malicious code is either detected or removed, the presence of secondary implants (most often hiding behind legitimate system services) keeps a back door and log-in open.
The intruder “hops” from the user’s machine into more critical servers by taking advantage of either misconfigurations or stolen credentials.
Instead of moving all data in one sweep (which is dangerous and noisy), an APT exfiltrates tiny files or packets over encrypted HTTPS channels that appear like normal web traffic.
Some of these groups eliminate traces of themselves to delay detection while others openly leave breadcrumbs to mislead the investigator about identity or origin.
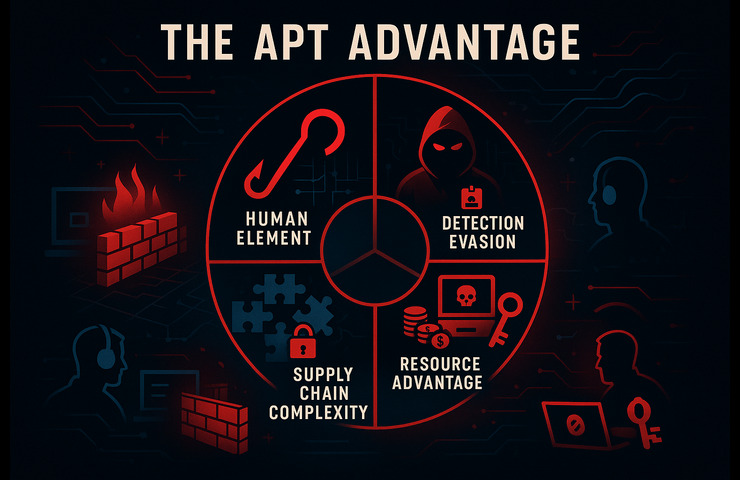
While only governments will be able to create widespread disruption of state-sponsored APTs, individual organizations can still raise the bar:
Security layers like MFA, firewalls, endpoint detection, and network segmentation are all intended to delay attackers.
Monitor abnormal process behaviors instead of just malware signatures; also check for anomalous data transfers to an unknown server or unusual log in activities.
Employees are better able to identify and report suspicious activity before it’s too late thanks to regular phishing simulations and transparent reporting channels.
Teams can reduce dwell time and damage by acting decisively when an intrusion is suspected thanks to tabletop exercises and clearly defined roles.
Keep a current inventory of hardware and software assets and check vendors for secure development practices.
APT groups are evolving as the attack surface expands with the Internet of Things (IoT), federal cloud utilization, and work-from-home.
Individuals and organizations must embrace and adapt to these trends and invest in safe and effective methods to protect themselves from streamed new APTs that may come as a routine part of our lives.
Takeaways APTs are a deliberate hybrid of technical capability, political determination, and tempered strategic thinking. The mystery may appear breathtaking, yet its anticipatory phases are predictable, and defenders can learn to recognize when and how APTs will burgeon. Whether you are a cybersecurity practitioner sharping your expertise or simply a regular individual looking for a summary, the importance of both innovation as well as the human factor, for the technical aspects of APT campaigns is valuable. Going forward, awareness and preparation are still our most effective options to deter against sophisticated, quiet adversaries in a connected world.
You may also like to read this: The Quiet Exodus of Trust: The Impact of Cybercrime on the Basis of Digital Society