
By Jayasurya Rajendrakumar, Jr. Security Researcher
IntelBroker is one of the most prominent threat actors in the world of cybercrime. This exceptionally sophisticated adversary has ruined countless bits of classified intelligence and documents from some of the world’s most secure networks—such as U.S. defense contractors and European law enforcement agencies.
However, who is IntelBroker? And how did this organization breach entities who spend millions on cybersecurity?
In 2023, IntelBroker showed itself to be different from the rest of the cybercriminals. They took a systematic and educated approach to cybercrimes, specifically outlining high-value organizations—such as government entities, Fortune 500 companies, and critical infrastructure providers—rather than hacking random systems on a hope and prayer for a quick payout. Every breach was intentional, tailored to strategic depth, purposeful, and planned to maximize subsequent damage results.
Their operational tactics regarding data exfiltration, stealthy infiltration, and public releases via dark web sites like Breach Forums, became known. The overt message was that no organization was safe from the wrath of IntelBroker, no matter the amount spent on cybersecurity.
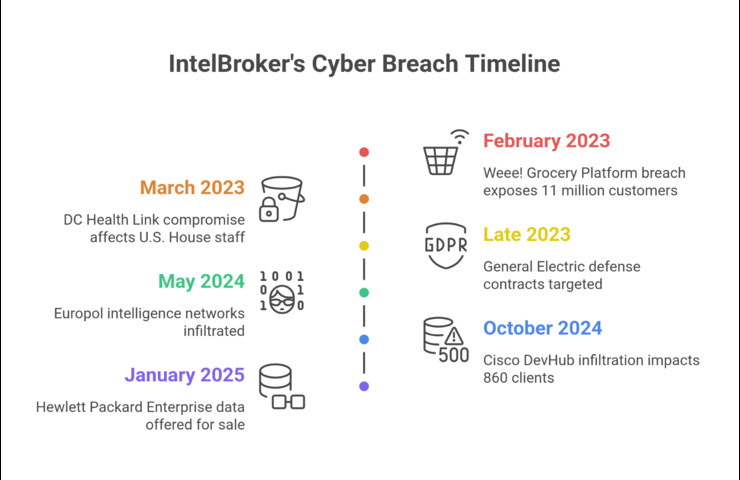
Grocery Marketplace Weee! (February 2023)
The first significant hack where IntelBroker actually came away with over 11 million customers’ data was a breach of the Asian grocery delivery service Weee!. The hack demonstrated how consumer platforms can be an entry point into larger campaigns, while payment data remained secure.
Impact: Highlight vulnerabilities in startup data processes and security systems.
IntelBroker’s first foray into government targeting began with the hack of DC Health Link, which provides health insurance to employees of the US House of Representatives. The breach exposed federal employees’ Social Security numbers and other personal identifiers.
Impact: Congress conducted security assessments after an initial, direct attack on the digital infrastructure that underpins the U.S. legislative branch.
IntelBroker took its aim at the defense industry by compromising GE systems containing data from DARPA military projects. The compromised material included source code, internal communications, and network credentials for U.S. military communications systems.
Impact: Increased national security concerns related to supply chain risks and cybersecurity for defense contractors.
Upon joining with a partner (Sanggiero), IntelBroker compromised Acuity, a contractor of U.S. intelligence-related activities. Included in the compromised information was purportedly communications from members of the Five Eyes intelligence alliance.
Impact: Documented ability to acquire access to sensitive international communications and exploit intelligence community contractors.
IntelBroker’s most audacious attack was to hack into Europol’s Expert Platform (EPE) and SIRIUS systems to gain access to internal documents labelled “For Official Use Only.” Europol later admitted that there was a serious security breach and that a breach had occurred.
Impact: Proven ability to acquire classified intelligence and breach continental law enforcement mechanisms.
IntelBroker breached Cisco’s development environment with a group of other threat actors, which provided them with source code, API keys, and SSL certificates. The attack affected over 860 business customers, including Microsoft, AT&T, and Apple.
Impact: Showed the potential for supply chain attacks and how cyberthreats are interconnected in the modern age.
The IntelBroker attack on HPE breached their internal development environments, took employee data, and retrieved source code. The stolen data was posted for sale on dark markets.
Impact: Reinforced the threat actor’s transition from data leaker to broker of initial access.
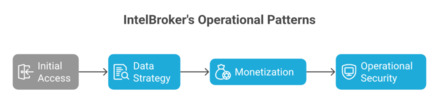
Intelligence Broker’s operational behavior provides insights into some advanced tradecraft:
Initial Access: Typically involved phishing operations, utilizing misconfigured cloud environments, and credential stuffing operations.
Data Strategy: Focused on high-value data sets such as repo source code, internal communications, authentication credentials, and personal identifiable information (PII).
Monetization: Utilizing public dark web marketplaces and typically asks for Monero cryptocurrency to provide para-transparency on transactions.
Operational Security: Only works with vetted underground actors, typically no reuse of digital infrastructure, strictly adhered to anonymity protocols.
In Jun 2025, US law enforcement arrested 19-year-old Kai West of Pennsylvania and charged him with being IntelBroker. West was charged with over 40 security vulnerabilities that caused an estimated $25 million in damage.
However, the cybersecurity community still disagrees about whether West represents the entirety of IntelBroker’s operations. Some analysts theorize the main threat actor is still out there, while others conjecture he may be part of a larger collective. Due to the complexity of the attacks and the global scope of the operations, it seems unlikely that a single individual could plan these types of campaigns.
IntelBroker is an incipient example of the emergence of modern cyberthreats, not merely a single cybercrime. Significant ramifications include:
There are pertinent lessons for organizations from IntelBroker into:
The emergence of IntelBroker signifies the beginning of a new age in cyberthreats where private actors can exert a strategic influence that was previously only possible through actions by nation-states. IntelBroker’s aggressive targeting of defense contractors, government entities, and critical infrastructure suppliers indicates how fragile modern digital ecosystems remain today.
Whether IntelBroker will cease operations now that Kai West is in custody is still to be determined. However, there is no doubt that the methods, goals, and impacts of this campaign will inform future offensive and defensive cybersecurity operations.
Organizations today must now ask themselves whether they have comprehensive security measures in place to detect and mitigate these types of attacks before they inflict significant damage, not if they continue.