
By Nirmal Kumar S., a researcher
We all understand threats like ransomware, malware payloads, social engineering and phishing initiatives in the cyber-threat environment. They are serious, without question, but can all be hunted. They leave tracks with which we can reference. They have pattern recognition.
However, there are threats that lie deeper than our understanding and comprehension.
The Dark Web is a private area of the internet where lawlessness thrives and anonymity is ever present. It contains sincere spaces for whistleblowers, and privacy-affirming practices, but the Dark Web is to an organized cybercriminal network unfathomably vast.
We went to this space as much to research as we did to see it. To research, instead of just read. We wanted to uncover what lay below, what we found was real and much larger and darker than we expected.
The dark web is not easy to define as one simple single phenomenon, but rather one whole cosmology of criminality. While there are differences, the would not be worth our time without categorizing them. The most common, and greatest dangers we found were
Arms and Ammunition: From stores with sales for operational firearms, to AK-47s, handguns, and explosives. Additionally, these listings often include crypto payment and location delivery.
Drugs and Narcotics: Legitimate shops with sales of various drugs like heroin, LSD, fentanyl, and methamphetamine; also, advertising purity scores and ratings from consumption reports.
Fake Documents and Currency: Complete identity kits prepared to carry out fraud, money laundering, and fake identification documents. Uses social media profiles, government, databases, and leaked facial generators.
Human Organs: Kidneys, livers, and other organs were available. The ramifications were unsettling even if the specifics were vague and no medical evidence existed.
Human Trafficking: A few people were able to purchase “people” primarily children from behind invite-only and encrypted walls. Posts and in reference to age and nationality, behavior; posters used emoji and codification.
Hitman Services: Several websites advertised, contract killing, with choices of weapons, location and even descriptions of target profiles. To enforce “guarantee”, some used reviews and escrow protection.
Child Exploitation Content: There were a limited number of specialized platforms that shared illegal content specifically involving children, and you had to dig very deep. These communities operated with crypto wallets, subscriptions and design their way of user interaction engagement.
Cybercrime as a Service: Everything you needed to attack a system was offered to you, even credential stuffing ‘kits’ and ransomware. They provided revenue-sharing platforms and “tech support.”
Fake Identities and Data: Complete identity kits are prepared to carry out fraud, money laundering, and fake identification documents. Uses social media profiles, government databases, and leaked facial generators.
Corporate Data Leaks: Legitimate business information which has been stolen, is traded on several marketplaces. This includes databases with customer information, internal emails, staff credentials, and even intellectual property. These leaks are often provisioned and sold to rival businesses, scammers and ransomware gangs. Some of the bids on entire company profiles for the sale underscores how serious a data breach can be when it gets to these clandestine marketplaces.
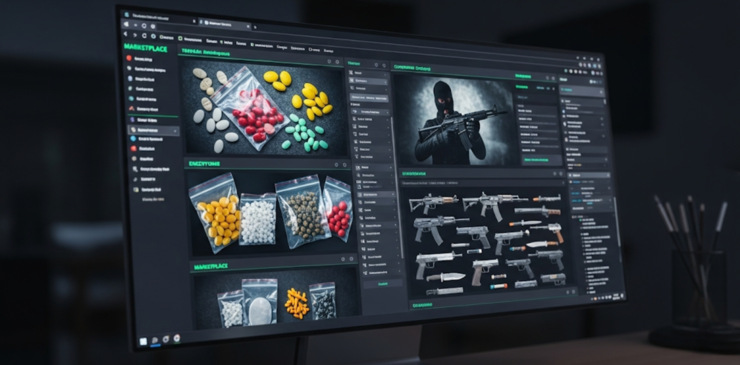
Through the scope and structure of these offerings we learned the dark web is much more than just a criminal underworld. It is a full digital economy.
While it may appear chaotic from the outside, it is ordered and professional in nature.
An aspect that is commonly overlooked is how dark web actors draw and keep users involved. For every criminal, there are several curious participants, idealistic actors, and those driven criminally by necessity across a plurality of situations.
In fact, what the communities do, using anonymity to incentivize participation, and providing support to build trust among members, is to promote participation.
Some forums also provide mentorship to new members, provide role-based permissions, and issue reputational badges. This “gamification” keeps people engaged and committed. During one case we were involved with a dark web ransomware group that had replicable corporate structure, and paid developer’s bonuses and salaries on a monthly basis.
Once you consider the psychological hold of these ecosystems, it is easy to see why their
resilience is incredible and why simple takedowns do not ever seem to matter.
Even if you never visit you may know on the dark web.
Staying safe does not mean you have to be an expert in cyberspace. Here is how to decrease exposure:
Lastly, support and trust ethical cyber investigations. Criminal justice, intelligence bureau, CSE or other cyber threats intelligence units, corporations, and organizations are in agency at the frontline of the digital battle obliterating corrupt networks, one trace at a time.
The dark web is, much more than a virtual underworld, a clandestine, complex, and global entity of crime that harms everything from corporate integrity to personal privacy. While we may never completely stop the dark web right now, going forward we can expose its landscape, declaw its effects, and potentially save lives. We are just getting started. To be continued…
Please reach out to our team if you are a company, nonprofit, or government organization that requires assistance spotting dark web threats or acquiring ethical cyber intelligence reports.