Safeguard your brand on Android with our app monitoring solution. Detect and expose malicious apps, track keywords, and ensure 99% coverage against brand misuse and impersonation, backed by comprehensive data analysis.

Saptang Labs' App Threat Monitoring provides real-time detection of anomalies and suspicious activity. AI-powered insights and alerts enable quick, proactive threat response.

Provides an in-depth analysis report outlining the behavior, origin, and malicious capabilities of detected malware, along with actionable remediation insights.

Leveraging the power of MITRE ATT&CK Techniques, our service provides automated reports that outline the tactics, techniques, and procedures.

We provide real-time visual evidence of malicious activity. This feature provides live screenshots of the malicious app in action, giving you direct insight into how the threat operates and its potential impacts.

We meticulously search for your brand logo within app assets. This helps uncover any unauthorized or fraudulent uses of your logo, offering an additional layer of protection against brand misuse.
Our service performs frequent data collection from multiple search engines, ensuring we identify any instances of malware payloads being downloaded under your brand's name.
We gather data on publicly reported apps from multiple sources, offering 99% coverage against brand misuse and impersonation.



We begin by aligning our system with your environment—mapping out the architecture, integrating your apps, and ensuring every component is ready for active monitoring. Our goal is a clean, secure start.
Your applications are monitored around the clock—no gaps, no blind spots. We track behavior, usage, and potential anomalies with precision and consistency.

We don’t just detect threats—we break them down. Every alert is analyzed for impact and origin, so you're equipped with the context needed to respond with clarity and control.

When something demands your attention, you’ll know—instantly. Our reporting delivers concise, actionable insights so your team can act fast and stay ahead.
Our Android app monitoring solution helps you guard your brand against cyber threats. Using extensive keyword tracking, in-depth malware analysis, and automated technical app reporting, we identify and expose malicious apps that target and impersonate your brand. Harnessing data from various sources and social media platforms, we guarantee 99% coverage against brand misuse and impersonation.
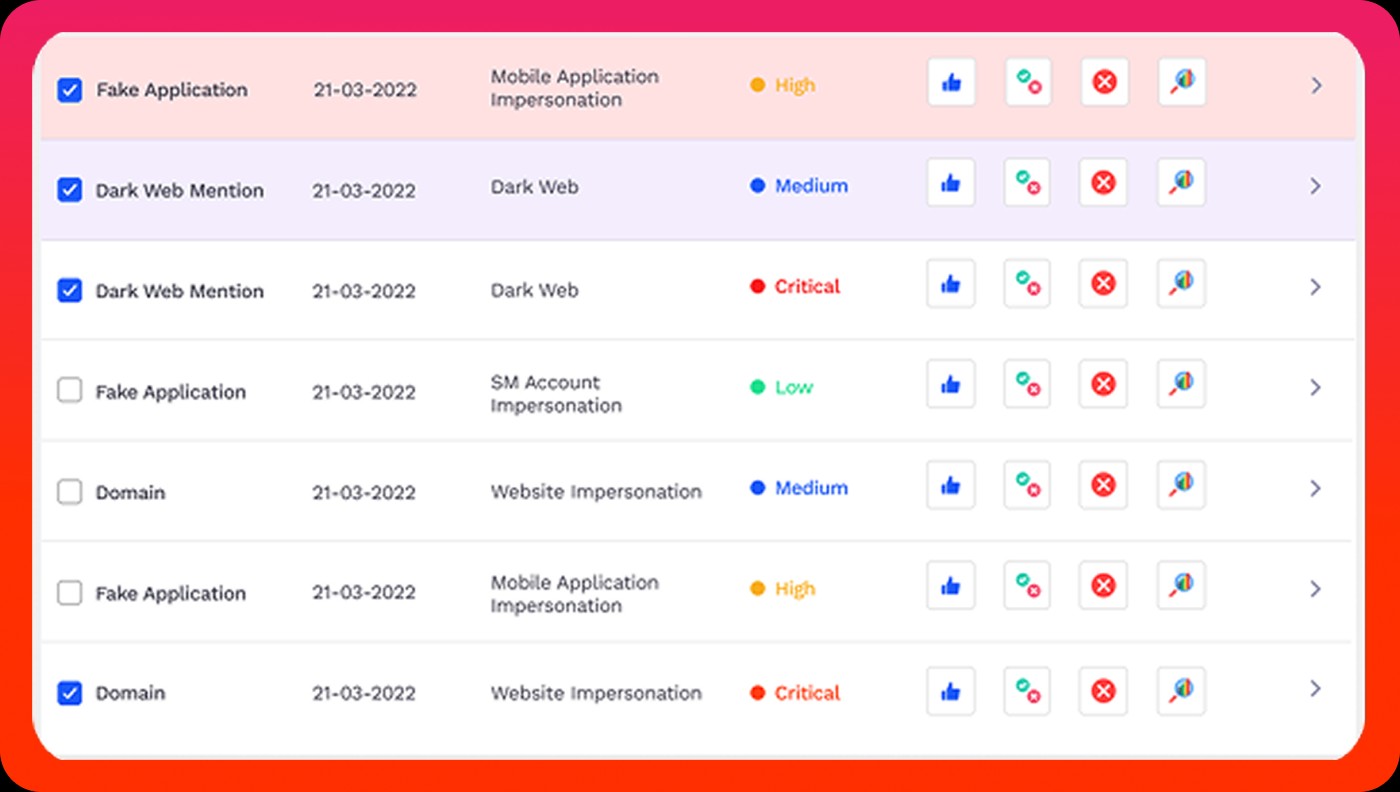
Our product actively scans app marketplaces, social media platforms, and other sources to detect emerging threats, ensuring that you are well informed and prepared to combat potential risks.
We provide in-depth analysis of malicious apps, offering valuable insights into their harmful intent, potential impact, and techniques employed.
We identify and track malicious apps and brand impersonations, enabling you to take prompt action against those attempting to exploit your brand identity.
Our product continuously monitors various digital platforms, providing you with real-time updates on any potential threats to your brand.
Our product generates detailed and insightful reports, summarizing threat analysis, risk assessment, and recommended actions in a clear and actionable format.
With our sophisticated analysis algorithms, we thoroughly examine app behaviour, code, permissions, and user reviews to determine potential risks.