Combat domain-related threats, including phishing and brand impersonation, with our comprehensive domain monitoring solution. Detect content duplication, logo misuse, and website defacement to strengthen your organization’s digital security.

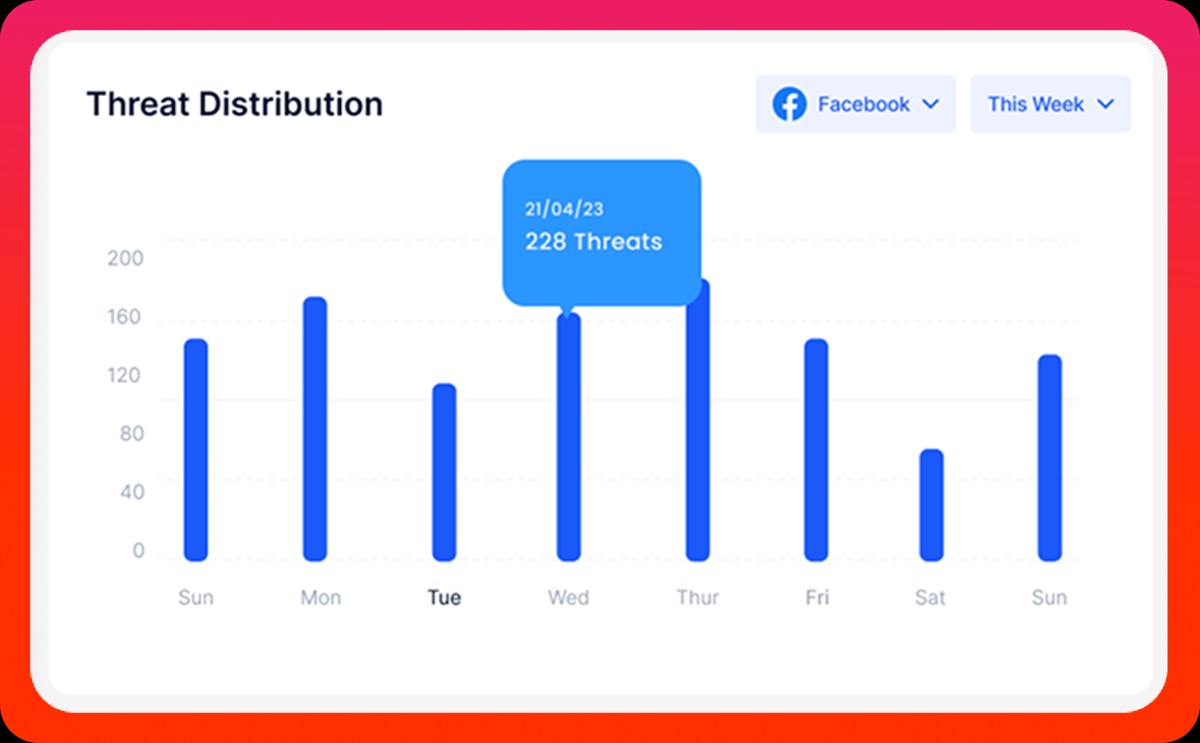
Domain Threat Monitoring tracks suspicious activities and phishing attempts on your domains, detecting fraudulent sites to prevent brand impersonation and protect your online presence.
Detects phishing domains by analyzing domain lists, public forums, and social media, securing your online presence.
Identifies malicious and impersonating domains, safeguarding your brand's integrity and customer trust.
Alerts you when similar content or images are used elsewhere, highlighting potential brand impersonation attempts.

Auto-tracks new and existing domains for suspicious activities, eliminating manual tracking efforts and reducing human error.

Aggregates data from various sources like Google search, social media platforms, and public forums for comprehensive threat analysis.

Proactively identifies attempts to misuse your logos and branding, ensuring your brand's authenticity is preserved online.



We start by identifying domains you own or rely on, configuring monitoring parameters, and establishing baselines for what's normal—and what's not.
We continuously scan for lookalike domains, typosquats, and newly registered threats that mimic or target your brand and users.

Each flagged domain is analyzed for intent—whether it's a dormant risk or an active attack vector. You get clear visibility into what's credible and what's noise.

We assign threat levels based on behavior, content, and associations—helping you prioritize which domains need immediate attention and which can be monitored over time.

Stay informed with timely updates. When a threat emerges, you'll know right away—backed by actionable insights and clear next steps.

We maintain continuous surveillance across all relevant domains, adapting to new patterns and threats as they emerge—so you're always a step ahead.
Our social media monitoring tool will help you to safeguard your brand’s reputation by identifying and taking down impersonating accounts, fake profiles, misleading videos, phishing posts, and potentially threatening discussions across social media platforms. With our powerful features, you can proactively protect your brand, ensuring a secure digital environment for your audience while taking immediate action against harmful content.
A common online threat where cybercriminals create websites that look like legitimate ones to trick users into providing sensitive information.
This occurs when individuals register a domain that closely resembles an established brand, often with typos or slight alterations, to deceive customers or profit from the brand’s popularity.
This involves creating a domain name, website, or email address that appears to be affiliated with a particular brand to mislead consumers or harm the brand’s reputation.
The presence of phishing sites, impersonation domains, or defaced websites can damage a brand’s online reputation, leading to loss of customer trust.
Malicious activities like phishing and malware distribution can lead to substantial financial losses due to fraud, data breaches, or business interruption.
Brands may face legal issues or penalties if user data is compromised due to phishing attacks or malware on domains associated with the brand.
Analyzing mouse tracking and activity can provide valuable insights into user behavior, allowing for accurate identification of bots. Bots often exhibit distinct patterns that differ from human users, enabling effective detection.
Effective bot attack detection and mitigation safeguards brand reputation by preventing data breaches, spam, and fraud, ensuring customer trust, confidence, and long-term success.
Utilizing mouse tracking and activity analysis minimizes false positives, as the system evaluates nuanced factors like cursor movement, click patterns, and scrolling behavior to accurately distinguish between legitimate users and bots, ensuring uninterrupted user experience.